Identity Verification vs. Authentication: What’s the Difference?
Identity Verification vs. Authentication: What’s the Difference?
Blog Article
In today's digital age, where information and transactions are increasingly conducted on the internet, copyright verification has become a key element of digital security. As cyber security threats grow and attacks on data get more sophisticated, ensuring that individuals are authentically who they claim to be is crucial to protect personal and corporate information.
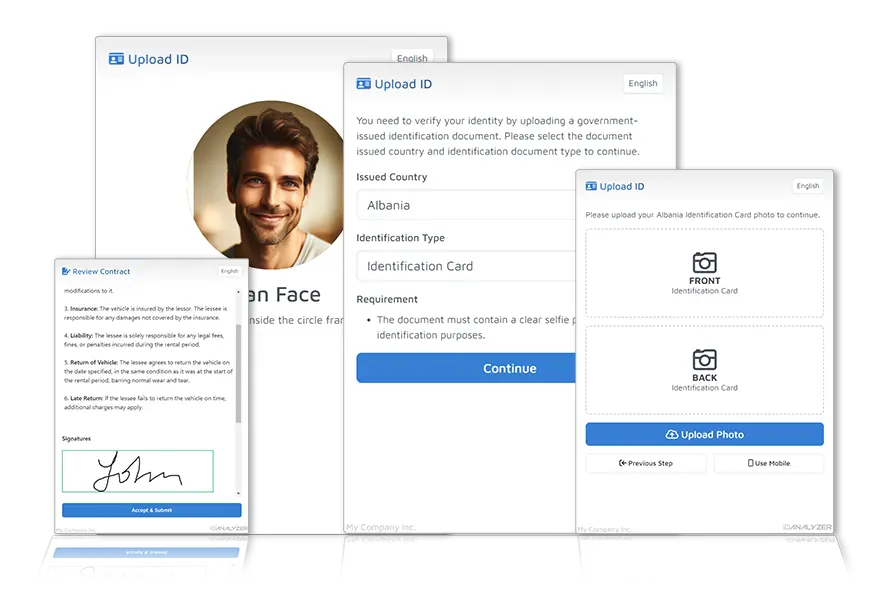
Understanding Identity Verification
The process of identity verification involves the process of verifying that a person is genuinely the person is they say to be. This can be carried out using various methods, including biometric information, passwords (like fingerprints or facial recognition), two-factor authentication (copyright) as well as more advanced solutions like blockchain-based systems. The main objective is to ensure that access to confidential information or systems is restricted only to authorized users.
Why It Matters
Prevention of Identity Theft and Fraud One of the biggest benefits of identity verification is its role in preventing identity fraud and theft. Cybercriminals frequently utilize weak or compromised authentication mechanisms to gain unauthorised access to accounts and other sensitive information. Effective identity verification methods, such as multiple-factor authentication make it much difficult for criminals to impersonate people or gain access resources.
Enhancing Trust and Credibility: For businesses and online platforms, strong identity verification processes enhance trust and credibility with users. When users are aware that their personal details are secure by rigorous security measures, they are more likely to interact with the website or platform. It is vital to build trust to keep a positive image and encouraging user loyalty.
Conformity with Regulations Compliance with Regulations: Several sectors are subject to regulations that require strict procedures for verification of identity. For example banks must abide with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations that requires thorough identification of their customers' identities in order to stop financial crimes. Infractions to these rules could result in serious financial and legal consequences.
Securely protecting sensitive data in the current climate where data breaches are increasingly common safeguarding sensitive information from access by unauthorized persons is essential. Identity verification can help ensure that only authentic users can access personal, financial, or private data. This is essential not only to protect privacy for individuals but also to ensure the security of corporate data.
Reducing the risk of operational risks for organizations, implementing efficient identity verification procedures reduces the risk of operational disruptions due to security breaches. Through confirming the identity of both users and employees, companies can stop unauthorized access to critical data and systems, minimising the risk of damage and ensuring smoother operation.
Challenges and Future Directions
Despite its importance however, identity verification is not without challenges. It is a delicate balance of security as well as ease of use is a major problem. Overly stringent verification processes could frustrate users and affect their experience. In addition, as technology develops as do the strategies of cybercriminals, which makes it essential to constantly modify and improve the methods for verification.
Looking ahead, advancements in technology, such as artificial intelligence and machine learning will play a significant role in enhancing identity verification systems. These technologies can offer more precise and effective authentication methods, thereby increasing digital security.
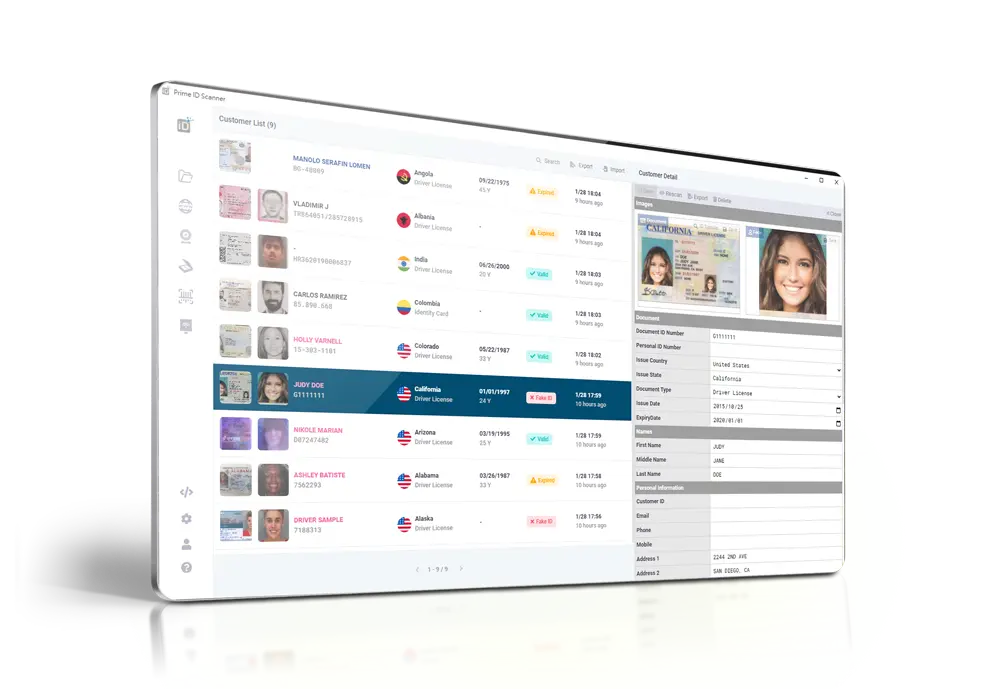
In the end, identity verification is an essential component in digital security. It safeguards against fraud, enhances confidence, guarantees regulatory compliance, safeguards sensitive data, and decreases operational risks. As digital threats continue to evolve, maintaining robust identity verification practices will be essential for securing our online lives.
Report this page